Passed on November 4, 2020, Proposition 24—now known as the California Privacy Rights Act (CPRA)—amends and bolsters the existing CCPA. The CPRA, which can be thought of as CCPA 2.0, makes data minimization a must for any business that does business in California, collects consumer data, and satisfies one of the following: has over $25m in annual revenue; makes more than half of its revenue from the sale of consumer data; or processes the personal information of more than 100,000 California residents or households.
The CCPA has been enforced since July 1, 2020, and enforcement of the CPRA is set to begin in July of 2023; however, there is a “look back” period that begins on January 1, 2022. Any data collected after this date will be subject to the CPRA, so if business leaders are not doing so already, they should prepare for the new obligations.
California Consumer Privacy Act (CCPA) vs. California Privacy Rights Act (CPRA)
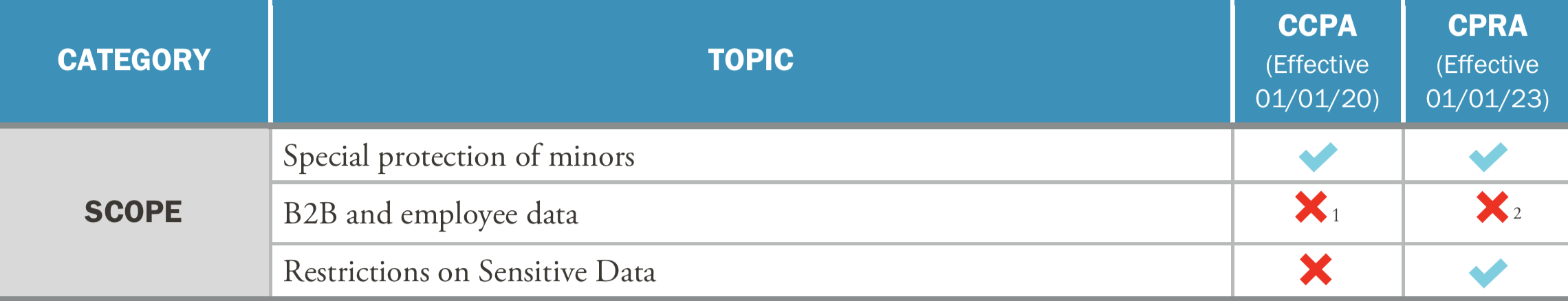
1. B2B and employee information exempted until Jan 1, 2022; 2. B2B and employee information exempted until Jan 1, 2023.
With a new category for “sensitive personal information,” data minimization is vital
Already a core component of the GDPR, data minimization is set to become an important part of the CPRA. According to Section 1798.100(c), the CPRA prevents businesses from collecting more personal information than is “reasonably necessary and proportionate to achieve the purposes for which the personal information was collected or processed.” Likewise, businesses are not to retain such personal information for any longer than is reasonably necessary [Section 1798.100(a)(3)].
The CPRA creates a new category for “sensitive personal information.” This includes social security numbers, driver’s license numbers, precise geolocation data, race, ethnicity, religion, sexual orientation, union membership, philosophical beliefs, genetic data, biometrics, and other health information. This is an extremely broad definition, making corporate data minimization (and data mapping) more important than ever.
The corporate liability for data breaches expands
Under the CPRA, data breaches will be particularly painful for companies that see their customers’ personal information compromised. The CPRA expands the existing law, allowing customers to bring legal cases against a company if their email address, password, or any other personal information is compromised during a breach.
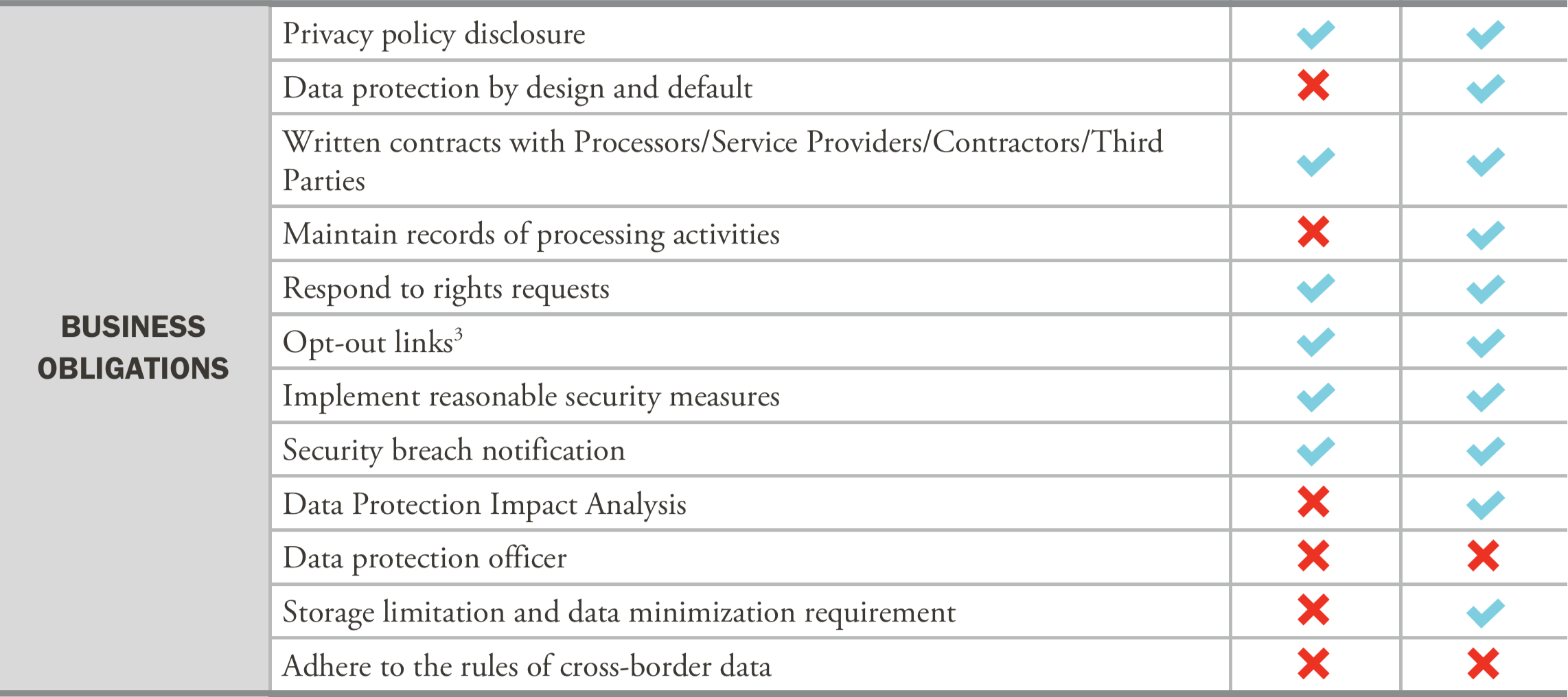 3. The CPRA expands the CCPA’s “Right to Opt-Out” to include not only the sale, but also the sharing of personal information. Businesses that share personal data are “covered businesses,” regardless of whether these businesses make money from this sharing.
3. The CPRA expands the CCPA’s “Right to Opt-Out” to include not only the sale, but also the sharing of personal information. Businesses that share personal data are “covered businesses,” regardless of whether these businesses make money from this sharing.
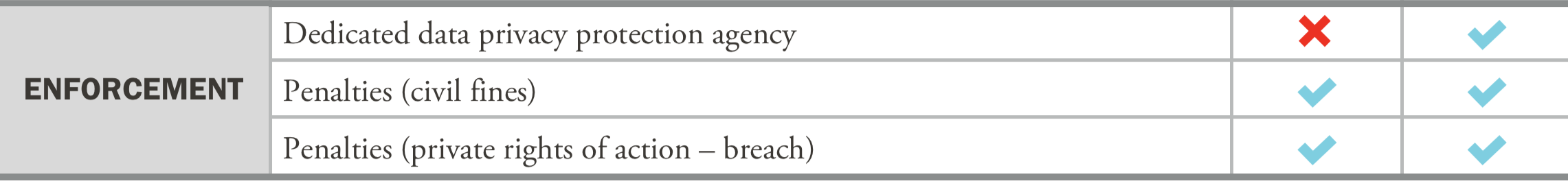
The creation of a new watchdog group
Perhaps the most obvious new provision of the CPRA is the creation of a new government agency tasked with handling compliance and enforcing the law. This California Privacy Protection Agency (CPPA) will be comprised of a five-member board, which will be announced later this year. Additionally, there will be a Chief Privacy Auditor who will be responsible for auditing businesses and liaising with European data protection agencies. Working on a three-pronged front, the agency will be tasked with additional rule-making, enforcement of the law, and some education initiatives. In regard to the education component, the agency will periodically allocate some of its annual budget to educating consumers and businesses about CPRA compliance.
We can expect to see more audits under the CPRA
If an organization processes enough personal information to be deemed a significant risk to consumer privacy or security, the aforementioned agency and the Chief Privacy Auditor will conduct an annual cybersecurity audit of the organization. Additionally, all high-risk organizations will be mandated to submit regular risk assessments to the agency as well.
With new provisions for automated decision-making technologies, consumer rights are bolstered
Under the CPRA, for the first time, consumers can opt-out of automated decision-making technologies. Consumers can inquire about the nature of the AI-based models your organization is using, as well as how their personal information is being used in such models. If any consumers object to their inclusion in these models, organizations must remove these customers’ data.
Consumers have more ways to restrict corporate data processing
Whereas the CCPA currently requires businesses to include a “Do not sell my information” link, the CPRA takes things a step further, mandating a “Do not sell or share my personal information” link, as well as a “Limit the use of my sensitive personal information” link.
The inclusion of “sharing” is an important modification of the CCPA. Under the CPRA, now covered businesses are responsible for not only the selling of consumer data, but also the sharing of such data. This includes any sharing of consumer data “to a third party for cross-context behavioral advertising, whether or not for monetary or other valuable consideration.” [Section 1798.100(a)(3)]
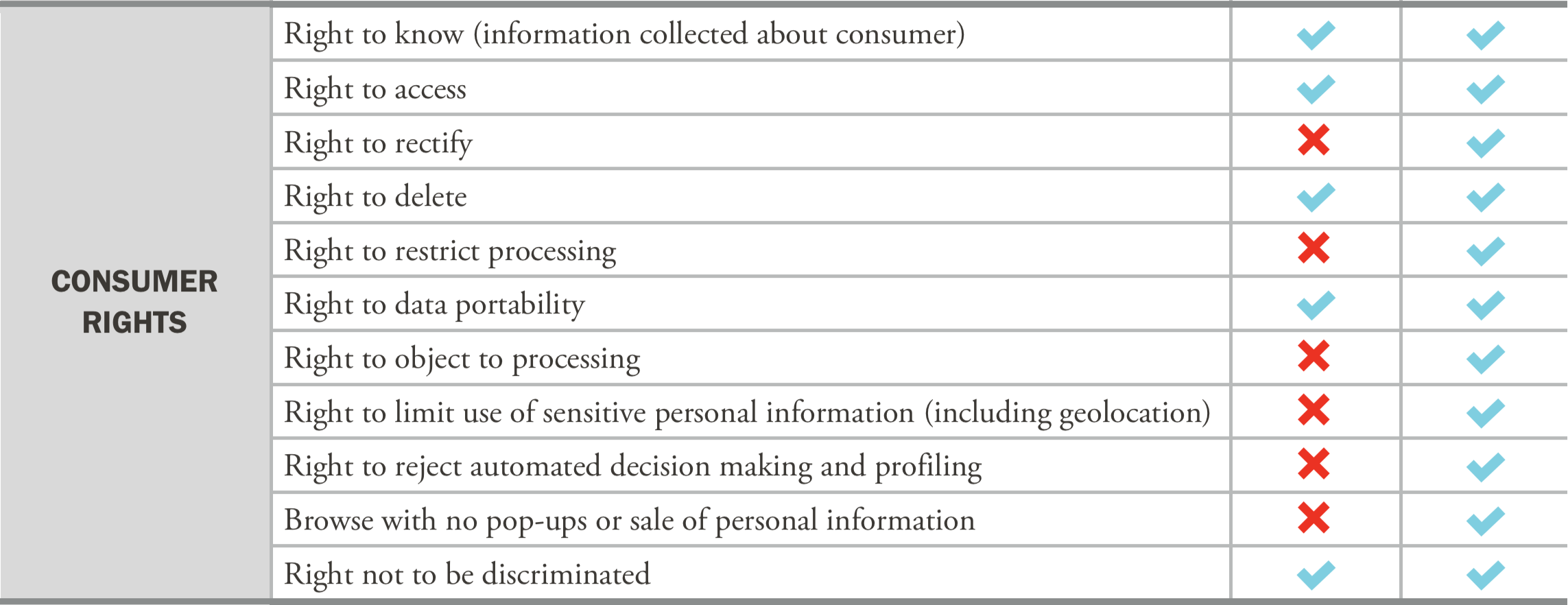 *Charts from Frost, Brown, Todd LLC
*Charts from Frost, Brown, Todd LLC
How best to prepare for the CPRA
If you’re already in compliance with the GDPR, you likely won’t have too much to worry about when the new regulatory agency begins enforcing the CPRA in July 2023. That said, the “look back” period is less than a year away, so it’s important to review your CCPA compliance and, if necessary, revamp your processes to meet the new requirements of the CPRA. Below are some suggested steps to take to ensure that your business will be ready.
1. Cut out all superfluous data collection. Much like the GDPR, the main goal of the CPRA is to ensure that organizations do not collect any more customer data than they need. As a best practice, be sure to only collect information on your customers that you absolutely need; make sure you only collect that data for the purpose in which you need it, and don’t keep any of this data for any longer than necessary.
2. Create a data inventory. Through the creation of a data inventory, you can maintain a handle on your data at all times. With a data inventory, you’ll know exactly what personal information has been collected and, importantly, why it’s been collected.
A data inventory will also help you account for retention periods—how long is the data being collected?—as well as the involvement of any third-party recipients—is the data being shared with any other organizations? To be sure, the creation of a data inventory is a crucial step in CPRA compliance, as it helps with audits and subjects’ access requests. It also helps you know exactly which applications and systems the consumer data is on, as well as whether these apps and systems are internal or external.
3. Track the trajectory of your collected data. Before the CPRA comes into effect, be sure to have your data flows in order. With data maps and data flow diagrams, you can effectively track the trajectory of your data. As mentioned earlier, companies need to ensure they are keeping track of any data that qualifies as “sensitive personal information” under the CPRA’s new definition.
Conclusion
Overall, the CPRA expands upon the CCPA, as it bolsters consumers’ rights; accounts for new algorithmic decision-making technologies, and takes a more comprehensive view of what qualifies as “sensitive personal information.” It also creates a new regulatory agency and expands the corporate liabilities for data breaches. To put it simply, if corporations are not already taking consumer data privacy seriously, they need to start. Although the law passed earlier in the year, it will not be enforced until January 2023. Nevertheless, we’ll keep you up to date on any additional changes as they come along.