In the past five years, the digital world has experienced unprecedented changes. While the physical world waged war against a deadly virus, the digital world thrived as a space for remote work, social interactions, and e-commerce.
As of 2023, 16% of all businesses have moved to complete and permanent remote operations, and by 2025, over 22% of the entire American workforce will have ceased to work on-premises.
While there are countless industries that cherished and perished from this sudden and drastic change, there was one that witnessed unrealistic growth—the cyber insurance industry.
To understand how that happened, let us look at the events of the early 2020s.
One small step for business, one giant leap for the industry
The hastened pursuit of a digital workspace came with a lot of straightforward benefits, like cost-cutting in terms of capital and logistics. But this came at the expense of leaving multiple IT network backdoors unchecked and unregulated.
This consequentially led to a plague of security incidents spreading over the digital world. Ranging from phishing and DDoS attacks to malware and viruses, and especially ransomware, data breaches ran wild throughout the digital diaspora. In 2020, one in six cyberattack victims faced a ransomware attack, and about half of them paid the ransom.
This is where it gets tricky.
If a company has an active cyber insurance policy during the attack, the insurer is liable to bear the fiscal demands of a cyberattack. In order to capitalize on such a crucial investment, all businesses with any form of digital presence rushed to purchase a cyber insurance plan. This led to the cyber insurance industry growing bigger than it was ever predicted.
The trend continues, and now, the global cyber insurance market has almost tripled in value over the span of three years. Even then, only 55% of all companies with an online presence have a cyber insurance policy in place. It now has a steady CAGR of 26.1% and is estimated to grow a sizable $84.62 billion in market share in less than 10 years.
But, there’s a catch!
Cyber insurers are losing money
Yes, you read that right. Though the global cyber insurance market will go down in history for having some of the fastest industry growth ever witnessed, individual cyber insurers are facing heavy losses.
Here are the numbers.
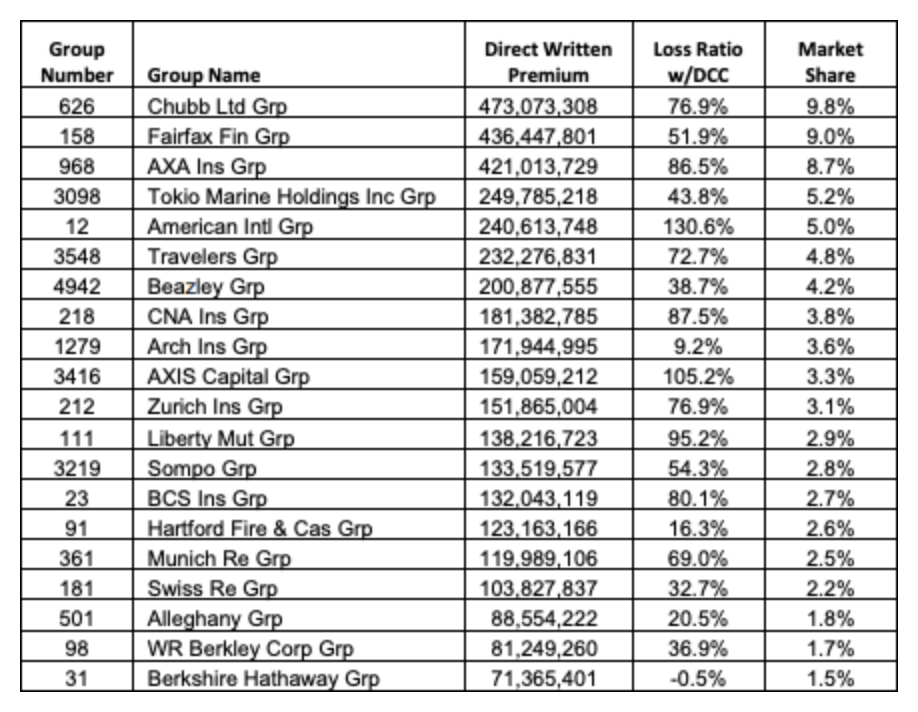
Source: The National Association of Insurance Commissioners, 2022
This recent report from the National Association of Insurance Commissioners (NAIC) the total amount of premiums written and the respective loss ratios of the top 20 United States insurance groups. Among the worst is a loss ratio of 130.6% by the American Intl Grp and a loss ratio of 105.2% by the AXIS Capital Grp.
Why is the loss ratio important?
The loss ratio is an insurance company’s total claims written, plus the insurer’s costs for handling those claims, divided by the total in premiums earned by the insurer—and this does not even include the overhead costs of running an insurance company.
To give you a fair idea of what the stats mean, ideally, an insurer would like to have a loss ratio of 40%. At 60%, things start to get a little tight. If it rises more than 60%, employees worry about losing their jobs.
The top 20 US insurers, who cumulatively hold over 81% of the market share, are at an average loss ratio of 60%. That means, though an exponentially high number of organizations pay for cyber insurance policies, the insurance companies are still losing money due to a high number of claims.
So, in order to find a solution to this paradox, cyber insurance companies decided to address the issue’s root cause: too many risky clients.
Stricter cyber insurance qualification metrics
Cyber insurers have been giving out more money than they’re making. This is because the majority of policyholders lack proper mechanisms in place to avoid a cyberattack. On top of that, the ransomware pandemic does not seem like it will stop. Insurers have realized their products are no fool’s gold and that every company ultimately will purchase a cyber insurance policy at some point, given the rapidly increasing interest to shift to a digital marketspace.
To mitigate the costs associated with claim delivery and execution, which have been unreasonably higher than their net revenue from premiums, insurers have decided to impose stricter metrics for a business to qualify for a cyber insurance policy. On top of that, cyber insurers have also increased premium costs to absurdly high amounts if a company does not have proper software and hardware in place to thwart cyberattacks.
Finally, insurers have also radicalized many underlying policy conditions to safeguard their interests.
Read the fine print
Some of these changes include the following exclusions, limitations, and conditions.
Ransomware exclusions
It is highly likely that your cyber insurance policy will have a ransomware exclusion. The primary driver for this change stems from the Office of Foreign Assets Control (OFAC) sanctions list. This list contains a set of institutions that are considered illegal to indulge in monetary transactions with.
Cyber insurers treat this sanctions list with utmost importance in order to avoid legal complications. Most companies that were unaware of the nature of such transactions have faced coverage denials, and therefore, it is important to understand the ransomware exclusion that is likely part of your policy.
In certain cases, insurers do process waivers for transactions that may or may not fall under the above-mentioned umbrella. However, these waivers usually take six months or more to be processed. Therefore, it is important to have sufficient reserves in place to keep your business functional should you fall victim to such a massive ransomware attack. These waivers also come with a presumption of denial clause.
Besides that, there is something called “strict liability” that cyber insurance policyholders need to be aware of. It’s a legal term that means even if you were unaware of the illegal nature of a ransom transaction, you could be held accountable and be charged under a civil suit for such a violation, for which you will not be covered.
Ransomware coinsurance and sub-limits
It would be laughable to assume that the number one sees on the first page of their policy document is claimable with no exceptions. Like any other insurance policy, it is safe to assume that sub-limitation clauses are buried in between the pages of your cyber insurance policy as well.
Typically, a sub-limit bifurcates how much coverage is available for a specific type of loss. So in the case of a ransomware attack, only a part of the total amount can be claimed if your policy has a ransomware sub-limit in place, which more often than not, it does. Additionally, if you have coinsurance clauses added to your sub-limit, you’ll also be obligated to cover a part of your ransomware expenses.
So, even though you might have a cyber insurance policy worth $10M, only 30% of that may be claimed in case of ransomware attacks, and moreover, even if the 30% covers your entire ransomware costs, you will be obligated to pay a percentage of the ransomware expense regardless when there is a coinsurance clause included in the sub-limit.
Legacy hardware and software exclusions
Different carriers use different definitions for the term legacy. Most of the terms used under such clauses are also almost always vague. We would advise policyholders to be careful and get clear distinctions between what their carriers consider legacy and what they don’t.
This, however, is straightforward in terms of implementation. Carriers usually don’t like gambling on legacy hardware and software given their outdated form and function and would advise businesses to upgrade to the latest versions of hardware. But certain multi-million enterprise IT infrastructures, like mainframe servers, could prove economically unfeasible to replace.
Even if your entire business model depends on the functionality of such legacy hardware, it will likely still not be covered by your carrier, depending on the policy.
Patch conditions
Unpatched vulnerabilities are excluded from your policy in multiple ways.
One way insurers do this is by determining how long it has been since the last patch was released for a particular vulnerability and how long it took the business to implement the said patch, while considering the severity of said vulnerability. Based on that timeline, you can expect the insurance payout amount to drop accordingly.
Zero-day exclusions
This exclusion means that if your business is hit with a zero-day exploit, the carrier is not obligated to satisfy the claim. We believe the presence of this exclusion should be considered a deal-breaker because it’s impossible to know when such an exploit exists. This exclusion certainly benefits the carrier, but from a business’ point of view, it does not make sense to subscribe to such a policy. We would strongly advise finding a carrier that does not enforce zero-day exclusions.
Business harm
Business harm is now uninsurable. If a cyberattack results in extended business downtime, this cost is now completely uninsurable by industry norms. There are, however, still some carriers who provide a small amount of insurance for business harm, but it can no longer be expected.
There are no accidents, only mistakes
All forms of data breach start at one place: unauthorized access. A fortified enterprise IT network boasting millions of dollars in resilience can be easily manipulated with something as simple as a leaked password or a vulnerable certificate.
The root cause of any major cyberattack almost always starts with unauthorized access to an enterprise identity, such as domain account passwords, server certificates, and cloud entitlements. Cyber insurance carriers recognize identity security and access management as crucial cogs of a business’ IT network strategy that help exponentially reduce possibilities of a data breach. They also mandate having such controls in place in order to meet cyber insurance qualification metrics.
At any given point, all IT networks have vulnerabilities, and one can never predict the downfall of a digital entity. Therefore, it is important to reverse-engineer your IT strategy to assume a threat always and enforce Zero Trust practices at any entry point into your IT establishment.











