When it comes to CISO budgeting, organizations tend to underinvest in cybersecurity initiatives. Intuitively, this makes some sense, as C-levels are often hyper-focused on cost savings. However, with debilitating cyberattacks becoming increasingly commonplace, it’s foolish to underspend on cybersecurity.
Through their now-famous study, two scholars from the University of Maryland’s Smith School of Business, Lawrence Gordon and Martin Loeb, developed a simple, yet groundbreaking model to help organizations balance their cybersecurity budgets. Although originally created back in 2002, the Gordon-Loeb Model is as relevant as ever today.
CISO budgeting can be a daunting task, especially for large enterprises; however, if you follow this model, you can simplify things and save time and money in the long run.
Step 1: Estimate the value of the data you want to protect.
According to Gordon and Loeb, information segmentation is key. While estimating your potential losses, it’s vital that you divide your datasets into different segments.
Step 2: Estimate the probability that each dataset will be breached.
Examine all datasets’ respective vulnerability: the probability an attack will occur and be successful. For example, if there is a 50% chance that your dataset will be attacked and a 40% chance of that attack being successful, your vulnerability score for that dataset will be (.5 x .4) = 0.2.
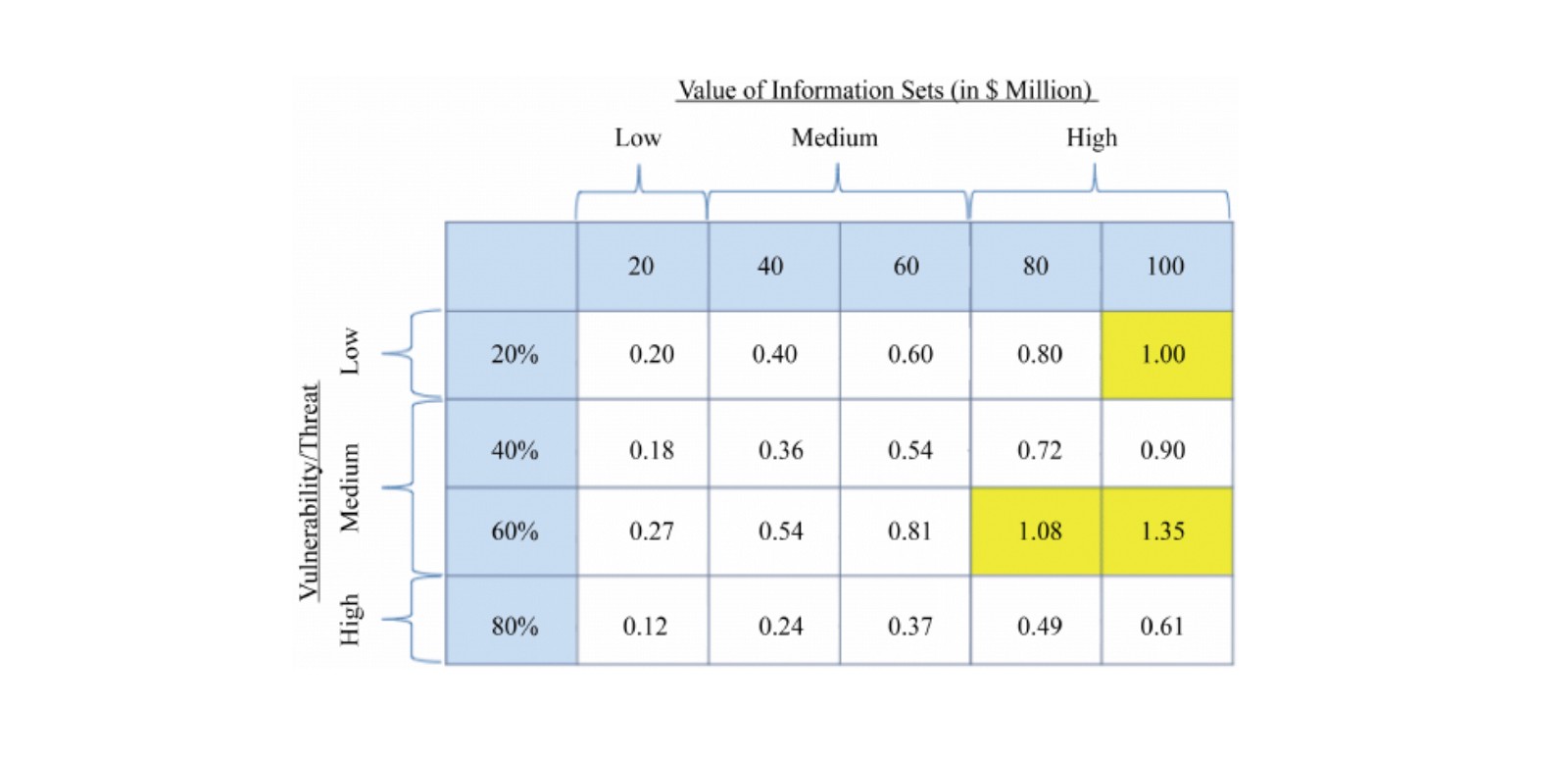
Step 3: Create a matrix with “data vulnerability” on the Y-axis and “value of the data” on the x-axis.
By creating a grid, it is easier to visualize exactly where you should allocate your cybersecurity funds. For each dataset within the matrix, multiply the value of the respective dataset by the probability an attack will be successful. This will allow you to quickly see where your most at-risk datasets are located.
Step 4: Spend your cybersecurity budget where it will be most productive—in terms of reducing your losses in the event of a breach.
Given that every box within the matrix now has it’s own potential loss value, it’s very easy to see where you should spend your CISO budget.
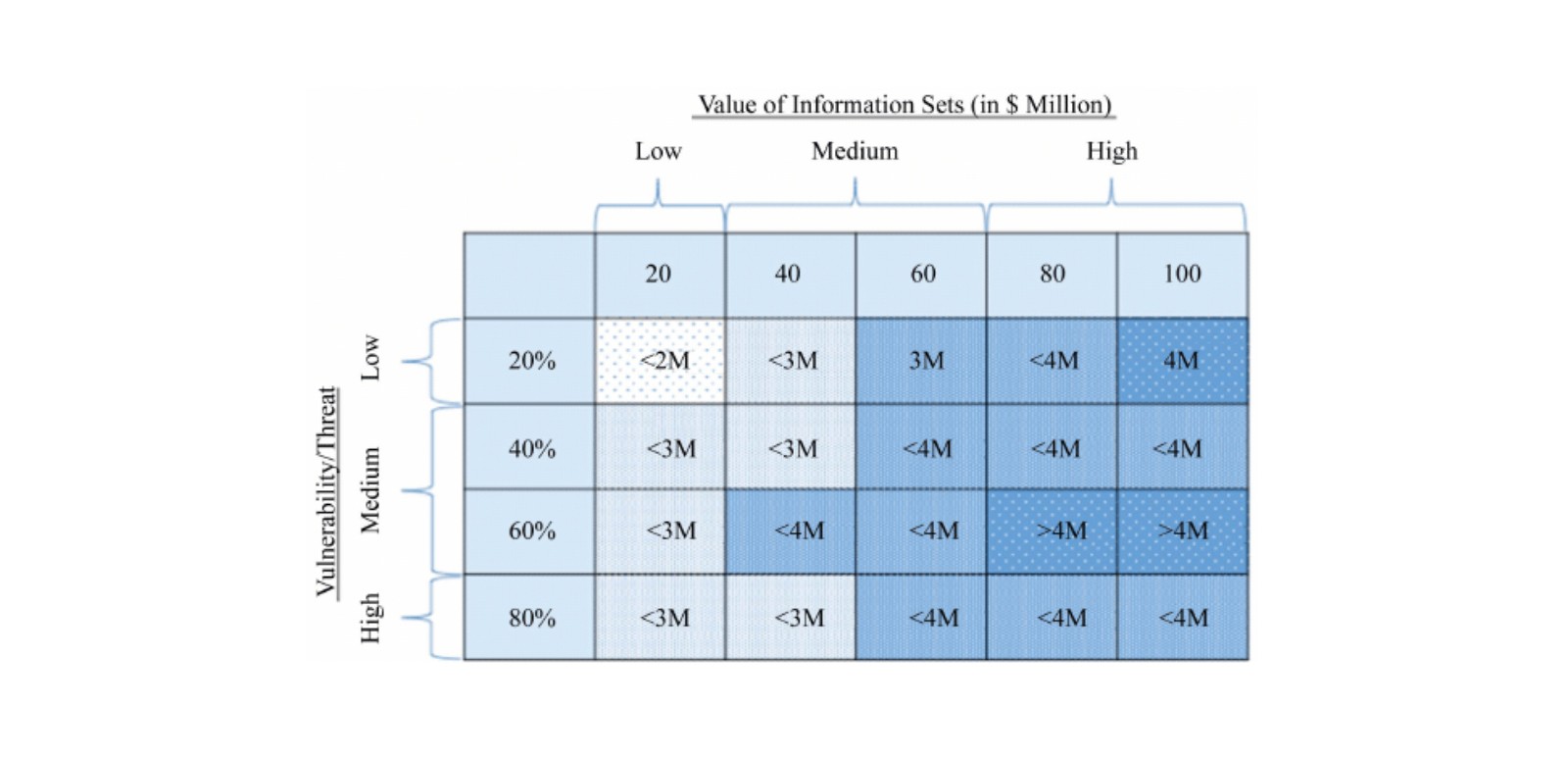
As a general rule, Gordon and Loeb found that after a certain threshold, cybersecurity costs begin to outweigh the benefits. According to the scholars, your CISO budget should never exceed 37% of your total expected losses. Although it is outside the scope of this article, the 37 percent comes from 1/e, which is roughly 0.367.
Example: Inside your matrix, a particular dataset has an attack probability of 20% and an 80% chance of that attack being successful. This would result in a “vulnerability score” of (0.2 x 0.8) = 0.16. If this dataset is valued at $3 million, then the potential loss is ($3m x 0.16) = $480,000. Then, seeing as you shouldn’t spend more than 37% of this number, you need to budget for no more than ($480,000 x .37) = $177,600.
Other Important Considerations
As a caveat, there are some additional factors to consider when coming up with your “vulnerability scores.” Breaches can inflict long lasting reputational damage. The aftermath of a bad breach can result in expensive class action lawsuits, serious fines, and untold damages due to exposed proprietary information. Breaches often have very long tails, so to speak, and they could prevent companies from engaging in M&A activity or public offerings.
Also, if your organization uses AI security platforms or runs a great deal of IoT devices, the fallout from a data breach will be different. According to the 2019 Cost of a Data Breach report from the Ponemon Institute and IBM Security, an average breach costs $148 per compromised record. That said, organizations that use AI security platforms save roughly $8 per compromised record, on average. By contrast, businesses that operate exclusively on IoT devices pay an additional $5 per compromised record, on average.
Key Takeaways
The Gordon-Loeb Model makes it very straightforward to conceptualize where to place your CISO dollars. Using this economic framework, it becomes much easier to justify your organization’s cybersecurity spending.
Although somewhat counterintuitive, it is not always cost effective to protect your most valuable assets. For a given dataset, if the probability of a successful attack is low, it very well could be cost prohibitive to protect these assets. Depending on how your matrix pans out, it might make sense to protect more of your less valuable assets.











