Now that the dust has settled, it feels like a good time to assess the recent Twitter attack that compromised 130 accounts, including those of prominent politicians and influential public figures.
Although many pundits initially speculated that the attack was conducted by foreign powers, it turned out to be the rather unsophisticated work of a 17-year-old hacker from Florida and two co-conspirators.
What happened: an account takeover campaign facilitated via social engineering
Through a phone spear phishing attack, at least one hacker convinced a Twitter employee that he was a co-worker in the IT department, which allowed him to gain credentials to Twitter’s customer service panel.
In total, the hackers gained access to 130 accounts. For 45 of these, they reset the users’ passwords, logged on, and tweeted from the account. Additionally, the bad actors accessed the direct messages of 36 accounts, and downloaded personal Twitter data from eight accounts.
The hackers initially tried to sell access to several accounts on the dark web. According to the New York Times, they attempted to sell accounts with “cool user names, like @w”; however, after selling the accounts, the hackers would subsequently reclaim access to the accounts, and kick the buyers out. Israel-based cybercrime intelligence firm Hudson Rock believes these transactions occurred at least 36-48 hours before Twitter and the rest of the world even noticed the breach on July 15.
Ultimately, on July 15, the hackers pivoted to the Bitcoin scam we’re now familiar with: they used popular accounts—like those of Joe Biden, Elon Musk, and Barack Obama—to solicit money from the accounts’ unsuspecting followers.
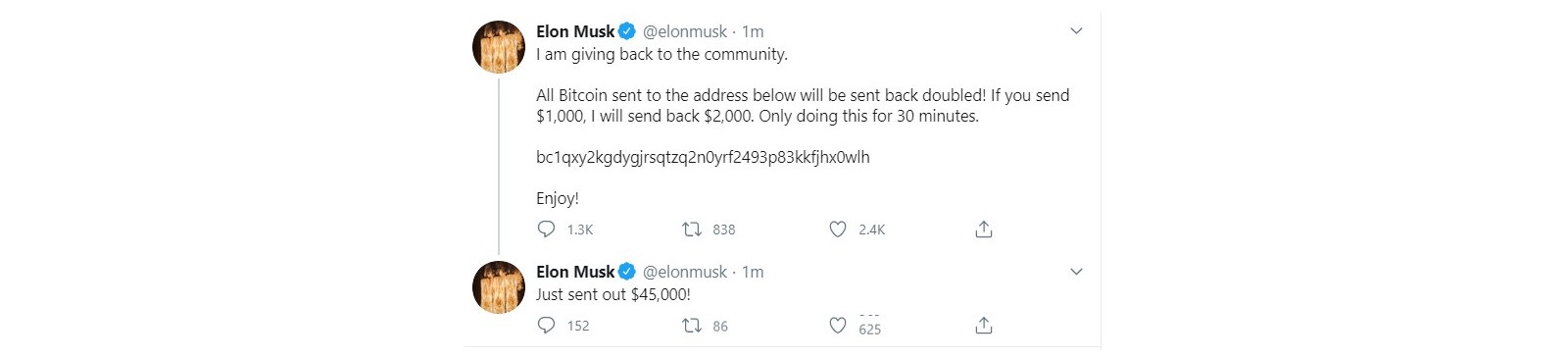
The bad actors made off with 12.98 BTC, or roughly $118,000. That said, it was by no means a successful hack, as the main culprit is incarcerated and facing 30 felony counts.
From a public relations standpoint, Twitter did a decent job addressing the breach and providing frequent updates. As quickly as possible, their incident response team was able to secure the internal systems; revoke the hackers’ access; disable all verified accounts, and lock any accounts where passwords had been recently changed. Nevertheless, the damage was already done—from both a reputational standpoint and a financial one.
The biggest lessons learned
As this case study shows, far too many Twitter employees had access to the company’s admin platform. By Twitter’s own admission, 1500 employees had access to Twitter’s “agent tools.” This greatly simplified the hackers’ social engineering efforts, as they had plenty of potential victims, and eventually one or two fell for the spear phishing attack.
1. Limit the number of employees with privileged access
In the aftermath of the attack, professional pentester Rachel Tobac emphatically tweeted, “I’m hoping companies all over the world learn from this example: attackers can’t leverage these tools if your employees don’t have back end access to make these account changes. Reduce admin privileges now.”
2. Consistently monitor the workers who do have access to backend systems
With privileged session monitoring, you can keep track of those few people in our organization with elevated access to important resources. By keeping logs of access to backend admin tools—and frequently reviewing these logs—you can quickly identify any unusual activity.
Additionally, through the use of privileged user behavior analytics tools, you can identify employees’ baseline behavior and then detect if he or she deviates from this baseline. As an example, perhaps a privileged user normally accesses the backend system from a certain location or certain time of day; any deviation from this baseline activity would automatically trigger an alert.
If Twitter had AI-driven anomaly detection tools in place, they could have potentially identified unusual access from an unusual location, allowing IT personnel to prevent the breach—or at the very least, reduce the incident response time.
Some tools even let you capture privileged users’ sessions and archive them as video files, which in turn can help in the event of an investigative audit.
3. Pair privileged users’ activity with event logs
Through context-aware event correlation, it is possible to monitor privileged administrators’ behavior and end user behavior simultaneously. For example, in the case of the Twitter hack, IT personnel could have recognized that end users—in this case, high-profile Twitter accounts—were tweeting similar messages. If this type of activity was flagged, as well as anomalous behavior from a privileged user, they could have expedited, and even automated, the proper incident response.
Although this hack was a public relations nightmare for the social media behemoth, the bad actors were ultimately caught and nobody was hurt. Moreover, and perhaps most importantly, the incident highlights the merits of adequate privilege access management software.











